Ha ha. Okay, it was closer to $35 for me, but I'm told if you wait for the right time, you can buy an Asus WL-520gU for $30 or less.
But the question has been asked of me, "Is this just a way of getting an Apple Airport without paying for one?", or "Why didn't you just buy an Apple Airport?"
Is this an Apple Airport Base Station replacement? Well, there are differences so it might not be a totally fair comparison. But the title was too catchy to pass up. I'm curious what those search engines are going to do. :)
Hardware Features and Cost
But first, just from a hardware point, we would need to compare models of Apple Airport with my device. Since the Asus WL-520gU lacks 802.11n, we would either have to compare with an older Apple model, or we need to bring in a newer model like the Asus RT-16N. The Asus RT-16N also has 802.11n, though it is a single band 2.4GHz so maybe this isn't an apt comparison either. I may need to go outside the Asus family for a better match up, though it must be remembered that DD-WRT also needs to be able to run on the router. Since 802.11n hasn't been a primary concern of mine, I haven't done my research in this area. The Cisco/Linksys WRT320N might be a closer match, but I haven't researched it heavily.
The Asus RT-16N also has 4 gigabit ethernet ports; the Airport Extreme has 3 gigabit ethernet ports. It also has 2 USB ports, whereas the Airport Extreme only has one. At a quick glance, the Asus RT-16N can be bought for around $90-$120. The Airport Extreme retails at $179. Apple stuff rarely goes on sale. (The Cisco/Linksys WRT320N seems to range from $70 to $130.) So the best Asus hardware equivalent is still considerably less expensive than the Airport. Though one cool feature I saw on a more expensive variation of Airport Extreme was the inclusion of Power-Over-Ethernet (PoE). I didn't see an Asus (or any of the other major consumer brands) equivalent of that.
Performance
As far as the actual performance goes for each such as wireless (or wired) real-world throughput, I have no idea since I've benchmarked neither. I suspect the Airport will be faster because of the dual band stuff. But if I were to find a dual-band competitor, my general experience has been to be unimpressed by any of these things. In the past all my devices have felt like commodities, completely interchangeable from a performance perspective. Performance was typically dominated by environmental effects and specific device configurations. Only Ruckus Wireless has ever stood out for me on the wireless portion. But I would be interested to see benchmarks on these actual devices. (Keep in mind, firmware versions may have an impact on performance.)
Bonjour (Zeroconf + NAT-PMP + Wide-Area-Bonjour + Bonjour Sleep Proxy)
As for software features, first, I have Zeroconf and NAT-PMP on the device. In theory, I think I should be able to support Wide-Area Bonjour.
I expect that my router will allow Back-to-My-Mac to pass through it, though I don't know if services directly provided by the router will be reachable since it isn't actually a Mac. I read Apple uses IPv6 and IPSec underneath the hood which I don't think these router firmwares completely support yet.
One thing I'm missing is Bonjour Sleep Proxy. (Though to be fair, my older Airport Extreme was not given a firmware update that includes Bonjour Sleep Proxy either.) I do wonder about whether I can successfully compile and run Apple's Bonjour successfully for my router. Apple does theoretically support Linux in their implementation. (I have successfully compiled and run Bonjour on my Linux desktop and also Sun Solaris (with a few issues)). I read that at least some of Apple's Airports also use Broadcom chipsets so hopefully that avoids any unexpected architecture issues. Bonjour Sleep Proxy is a really cool idea.
Network Attached Storage (NAS)
Airport Extreme also seems to imply you can use network attached storage for Time Machine. Apple sells a separate device called Time Capsule that does the same. I haven't studied up on the issue, but I recall there were some early serious problems with using the Airport Extreme with NAS as a Time Machine backup location. I don't know if these problems were resolved.
NAS seems to be a very popular thing to do with the Linux firmwares. I would guess setting up a Samba server is the most common way to do this.
But to go one step further, the question Mac users might ask is if the non-Apple NAS can be used as a Time Machine backup location. I think I have read that this can be done over Samba or NFS and the Mac only needs to write to a sparse disk image for its backups. But I also saw there were some people installing an AFP server (via Netatalk) so they could do network Time Machine backups for their Macs too using NAS. However, I read these also had serious problems because a few critical APIs were not implemented in the open source AFP implementation which were critical for handling cases when the drive filled up. So once your disk was filled, your data could become corrupt. From more recent posts, it sounds like this problem may have been resolved. But I don't have any first-hand knowledge of any of this.
Printer Sharing
Both Apple and the Linux firmwares seem to support printer sharing through the USB port. Presumably we should be able to setup Zeroconf advertising for the printer on our Linux firmware. But I don't know if Back-to-My-Mac will be able to connect to the printer through either Airport or our Linux router. If Back-to-My-Mac does work with only Airport, to be fair, it is worth pointing out that Airport does not support any other Dynamic DNS services.
Firewalling
I noticed a popular tool in Optware is Asiablock. Asiablock can be used to block all access attempts from IP addresses originating from countries in Asia (user configurable of course). There is another tool called Worldblock that extends the idea to all countries. As far as I know, Apple Airport doesn't give you any control like this.
VPN
Apple lacks VPN support. These are kind of niche things so I can see if Apple is targeting mainstream end-users, I can kind of understand them leaving it out since these features are fairly complicated to actually set up. But Apple also seems to target non-home-users in some cases with their Airport Extreme which makes this decision more questionable.
UPnP
But the Airport Extreme lacks one big feature that is really important for many home consumers. That feature is UPnP. Apple obviously supports NAT-PMP. But they don't ship with a UPnP fallback. A comical analysis might suggest that they looked at UPnP and decided inventing NAT-PMP and getting the entire industry to adopt it as a new open standard would be easier and saner than actually implementing UPnP themselves. Even though I am impressed by how many applications have already included NAT-PMP, unfortunately, there are still a few remaining mainstream things that use UPnP and it doesn't look like they are going to support NAT-PMP any time soon. Currently, the two biggest are Xbox 360 and Playstation 3. (I haven't been able to tell if Wii is also an issue.)
Searching the web, this seems to be a thorn for people with Xbox 360 or Playstation 3 behind an Airport. And while I think it may be possible for Sony and Nintendo to include NAT-PMP support in future versions of their devices, given Microsoft's track record, I expect them to refuse to embrace NAT-PMP for completely political reasons at the peril of their users. They have continued to reject Zeroconf in favor of pushing their own design which has pretty much been rejected by the entire industry since Apple's proposal was built completely on existing internet standards and already is distributed, adopted, and proven. It costs Microsoft nothing to say, 'thank you for inventing this open standard that everybody can use' and then use it to make the life of their users better. They don't have to pay anything to Apple and they are free to implement their own version based on the open spec if they are really paranoid about completely owning the source code to the things they ship. But there is no logical reason for their resistance to this, and I expect the same attitude for NAT-PMP. (Meanwhile, Windows customers sick of this BS can install Bonjour for Windows from Apple to at least get Zeroconf.)
On the flip side though, Apple should be used to being the odd-man out and needing to implement/support Microsoft protocols. (Exchange, anyone?) Since there are open source implementations of UPnP like MiniUPnP, there isn't a lot of excuse for them to not include it in their Airports.
Since there are a lot of Xbox's and Playstation's sold, I think this might be a deal breaker for many people. Port forwarding could be used as a work-around, but as I already stated in an earlier part, port forwarding has tons of downsides and isn't a perfect replacement. Airport also seems to lack port triggering. And since the cost of an Apple Airport is so much higher, it's really hard to justify the added expense for these users who benefit from UPnP.
User Interface
Finally, I should give a brief mention to the UI design. Apple lacks a web gui and instead builds a native GUI client to configure their devices. The upside is they tend to give a much more compelling UI experience. The downside is that it is only available on Mac OS X and Windows. (Sorry, no Linux. Heck, no iPhone either.)
As for UI, Apple's is pretty nice. DD-WRT, while not bad, still has areas that suffer from poor areas of UI design. I'll give one example.
I want to prevent anybody from reaching the DD-WRT web gui from the outside world. So I presume I want to disable all remote access. I see there is a list of checkboxes for each service. But at the end of the list, there is this confusing parameter "Allow Any Remote IP".
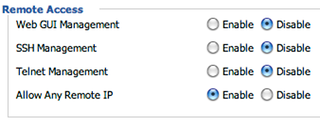
My instinct is that I don't want anything to access my router from the outside so I want to disable this feature. But then the GUI transforms into the following picture.
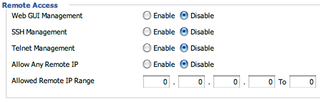
So now I am expected to enter an allowed IP range. But I don't want anything. This is confusing. I'm not sure if 0.0.0.0 has any effect or not. I don't know what the DD-WRT conventions are.
This could have been a little better if they just grayed out or removed the "Allow Any Remote IP" entry once I disabled all the individual services. I might go one step further and suggest they have a higher-level, encompassing checkbox called "Allow Remote Access" which subsequently removes or grays out the other options when disabled.
Summary
My motivation was not to actually build an Airport substitute. However, there are many overlapping areas. But there are actually enough key features that Airport doesn't provide, that for my current needs, the Linux firmware routers exceed the Apple Airport. That added with the lower cost is a win for me. Though if I only needed the features Apple provided, time-wise, I would have been much better off buying an Airport despite the additional cost.
Next time I will wrap up my experiences with DD-WRT, irrespective of all the Apple Airport comparisons.
Links:
Part 7: Installing MiniUPnP (previous)
Part 9: Conclusion (next)

